Thoughts on Email & First Things First
First Things First is a self-help book written by Stephen Covey. If you haven’t read it, I highly recommend it.
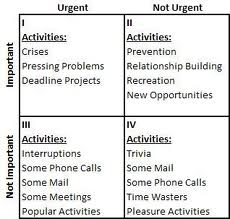
In the book, Covey describes a framework for prioritizing work that is aimed at long-term goals, at the expense of tasks that appear to be urgent, but are in fact less important. He uses a time management formulation attributed to Eisenhower (see: The Eisenhower Method), categorizing tasks into whether they are urgent and whether they are important, recognizing that important tasks may not be urgent, and urgent tasks are not necessarily important. This is his 2×2 matrix: classifying tasks as urgent and non-urgent on one axis, and important or non-important on the other axis.
This got me to thinking about how our anti-spam solution is able to map my email messages to this matrix. Sendio only delivers Urgent & Important messages to my mobile device; this means that I am able to enjoy life (without interruption) while still being alerted when appropriate (like a question from a customer, a notification about a down server, security-related messsages, etc.). When I have time, I am able to review my Sendio Hold queue to see if there are any new partnership opportunities (or the like) that I would like to take advantage of; these messages are Important to me, but Not Urgent. Finally, I am able to have all Not Important messages Dropped by the Sendio. (Of course, Bulk messages can be dropped automatically.)
I bring this up, because early last year Gartner published its, likely, last Magic Quadrant report on email security vendors. The maturity of the market, lack of competition, and commoditization of the products available, all pointed to a market where innovation was dead and so too the need for analyst reports.
However, Gartner researchers made a parting dig at the vendors who had failed to improve:
“Dissatisfaction with current bulk email capabilities is a significant pain point of existing solutions. End users don’t care about the clinical definition of spam and are frustrated with the level of “unwanted” email in their inboxes…None of the vendors offer personal controls to enable end users to better manage their inboxes.”
Sendio Opt-Inbox™, introduced in May of 2014, provides these exact features that offer end users complete control of their email inbox. If you are interested in removing the “noise” from your email inbox, please call (804) 798-4444 Option 2 or email sales@computer-business.com.