It’s 10 p.m. Do you know where your metadata is?
As our industry pushes toward “the cloud”, I question whether or not people know where their metadata is.
The example that I give is wireless local area network (WLAN) metadata. Back in the day, when we were selling Bluesocket to the likes of VCU, all WLAN metadata was housed at the customer site.
As “cloud” wireless solutions have become fast, easy, and cheap, we see them being deployed more and more frequently. But, when people deploy “cloud” wireless, I often wonder if they consider that all of the WLAN metadata is housed in the cloud.
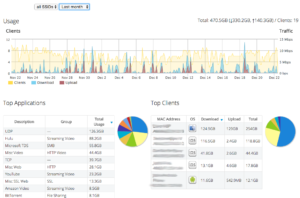
To illustrate my point, I requested permission to use a screenshot of a colleague’s “cloud” wireless dashboard; it is below. At a glance, the trained eye can tell that a macOS device is being used for BitTorrent. (I am not accusing said colleague of anything, I am just pointing out that only 0.3% of files on BitTorrent are confirmed to be legal.) I am sure that the DMCA folks would love to have a list of the MAC Addresses being used for BitTorrent.
So that this doesn’t sound too much like conspiracy theory, I am not accusing “cloud” wireless vendors of cooperating with ex-wives and divorce lawyers. But, I would not put it beyond the realm of possibility for this data to be easily accessible by some of Edward Snowden‘s former coworkers.
My call to action to you is to consider privacy when purchasing services in the cloud. Know where your data is. And, know where your metadata is.
Whether you have no idea what this article is about or have a highly technical question, we are always here to help: (804) 798-4444 Option 2 or sales@computer-business.com.
Until next time…